On January 12, 2026, the Qilin ransomware-as-a-service crew, also known as Agenda, refreshed its dark web leak site. The group claimed it had compromised four US organizations and published samples of stolen data as a warning shot ahead of a potential full release. In the ransomware world, getting listed on a leak portal usually means one of two things: negotiations are stuck, or the attackers are turning up the heat by threatening to dump the files publicly.
One of the newly named victims is Hayden Safe & Lock Co., a business focused on physical security, safe sales, and lock installation. The irony writes itself: a company built around protecting assets in the real world apparently could not keep its digital perimeter out of a ransomware crew’s hands.
Another notable target is G-Way Microwave, an American manufacturer of microwave electronics and components. When a manufacturing operation like this gets hit, the risk is not limited to downtime. Beyond encrypted systems, there is the very real possibility that sensitive internal material was accessed, from technical documentation and design files to customer and partner data, especially if the firm sits anywhere near telecom supply chains.
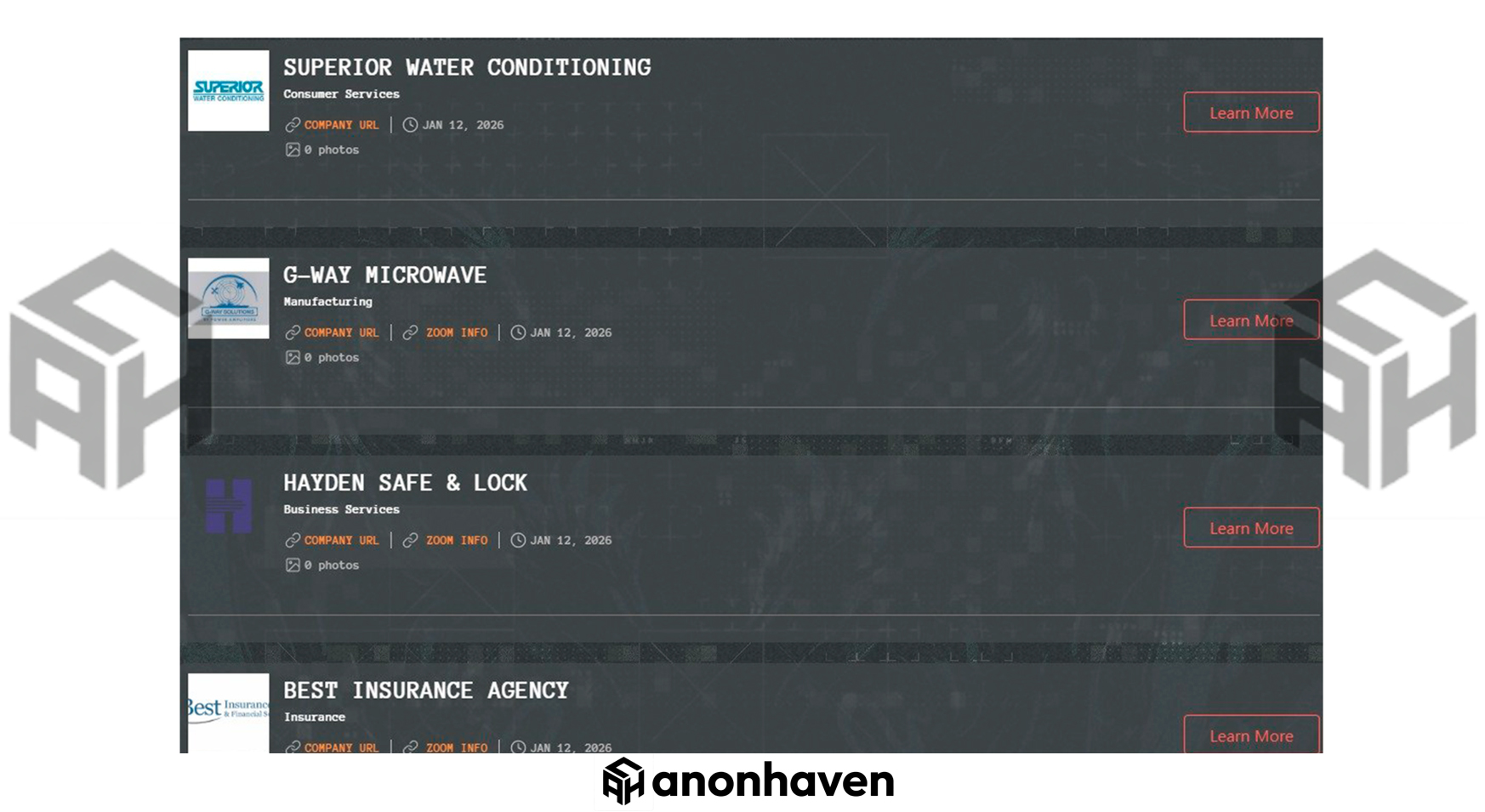
Qilin also listed Best Insurance Agency and Superior Water Conditioning, a company providing water treatment system services. Insurance-related operations are often attractive because of the volume of personal and financial information they handle, while service companies can be easier to disrupt due to sprawling remote access, weak segmentation, and legacy systems that were never designed to withstand modern extortion pressure.
How Qilin operates
Qilin runs a ransomware-as-a-service model paired with double extortion. The playbook is simple and effective: steal data first, then encrypt the environment. That way, even if a victim can restore from backups, the attackers still have leverage in the form of stolen files.
A leak-site listing is usually the pressure phase. It signals that the group is prepared to publish, or already has begun publishing, data to force a decision from leadership. The initial exposure often functions as a teaser, meant to prove the breach is real and to raise the cost of saying no.
In other words, this is not just another ransomware headline. It is the modern extortion stack in plain sight: operational disruption on one side, a reputational and legal minefield on the other, and a countdown that starts the moment your name appears on a dark web leak page.




