
On January 13, 2026, Dark Web Informer analysts spotted a telling listing on a shadow marketplace. An initial access broker using the handle powder12 is selling full administrative access to the server of a US tax services company. The price is $3,000, for control over infrastructure that likely contains sensitive data on thousands of citizens.
According to the listing, the compromised asset is a public-facing website and a client portal used for tax case management. The company has reportedly operated for more than 15 years, which usually means one thing in this business: a deep archive. Tax portals do not just store a single season. They accumulate historical records, family information, uploaded documents, and ongoing communication with consultants. For an attacker, that kind of archive is not noise. It is a ready-made identity theft dataset.
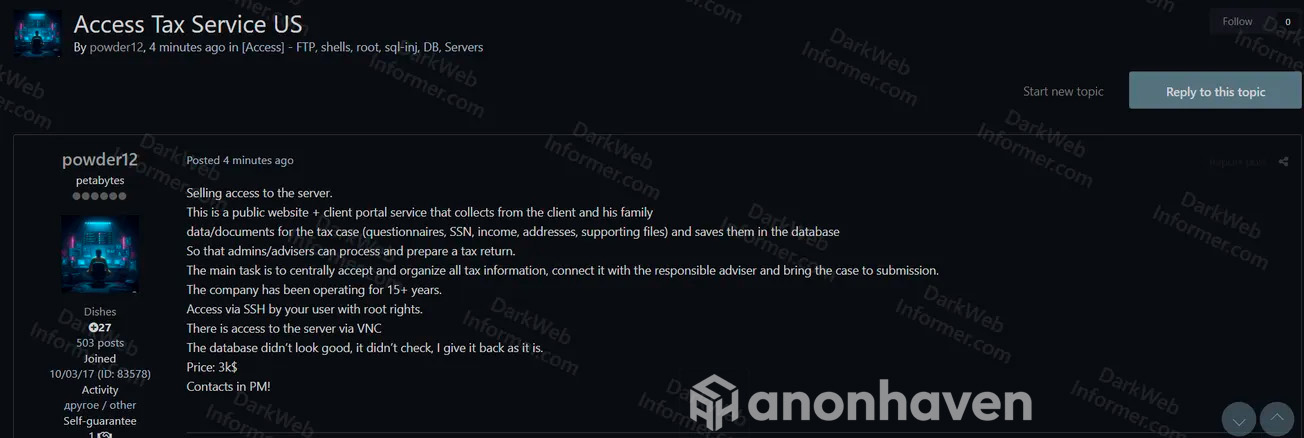
The seller claims the server holds data that is highly useful for fraud, including Social Security Numbers, income records, residential addresses, completed questionnaires, and supporting files. The listing suggests this material sits in a database that administrators can access during tax return processing, which is exactly the access level an intruder wants. With admin privileges, you do not need to guess what is valuable. You browse it.
The technical offer is straightforward and blunt. Powder12 is advertising root SSH access, the highest privilege level on the system, provided via an account. An alternative access method is also mentioned: VNC, a remote desktop-style channel that can be convenient for operators who prefer a GUI foothold.
The most striking detail is the price. $3,000 is low for a tax services portal, especially in January, when tax season pressure starts to build and business continuity becomes leverage. The seller does not pretend this is a careful, high-touch operation. They openly admit they did not inspect the database in depth and are selling access as-is. Original comment: didn’t check, I give it back as it is. That is typical IAB behavior. They optimize for speed. They sell the door key, not the stolen valuables inside.
This is exactly why listings like this matter. Root access to a tax platform during peak season is a gift to ransomware crews. With superuser privileges, an attacker can exfiltrate entire databases and then encrypt servers, forcing the company into downtime when every hour is expensive and every missed deadline turns into a client crisis. At this price point, a buyer is likely to show up fast.




